Using SMS for two-factor authentication offers nothing except a false sense of security.
You should be using two-factor authentication on every single online account you have. It doesn't matter how rich or how famous you are (though the rich and famous should probably do even more to secure their identities) because everyone has something of value hidden in their online accounts. Companies like Google and Facebook offer everything for free because our online data is so valuable.
Using two-factor authentication (2FA) isn't designed to be easy because proving that you're really who you claim to be should have a barrier attached. Unfortunately, many people think this barrier is too high or too inconvenient and skip 2FA altogether. I'm not going to stand on a soapbox and explain how wrong that is because that's been done to death. You know why you should use it and have made a decision.
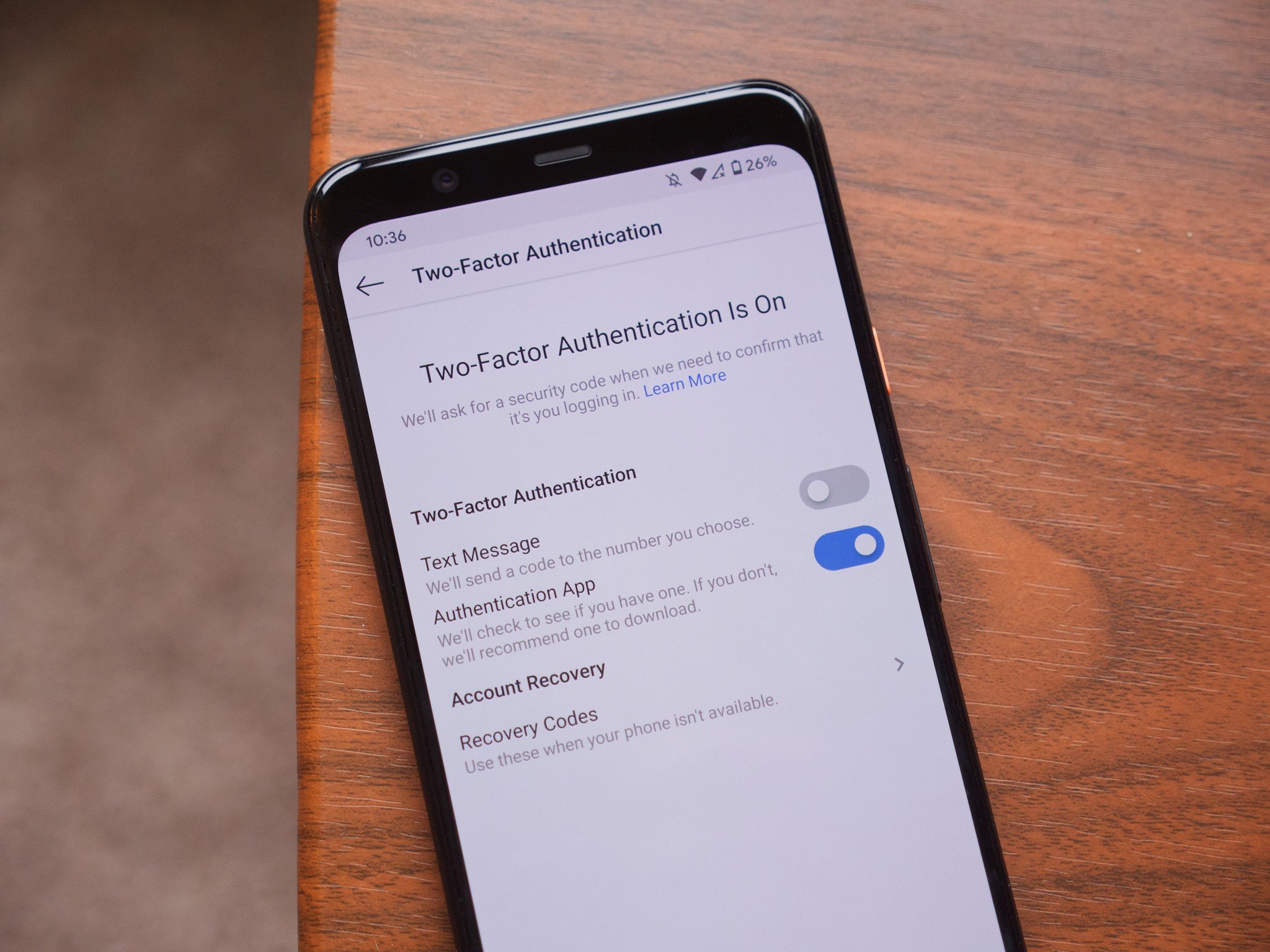
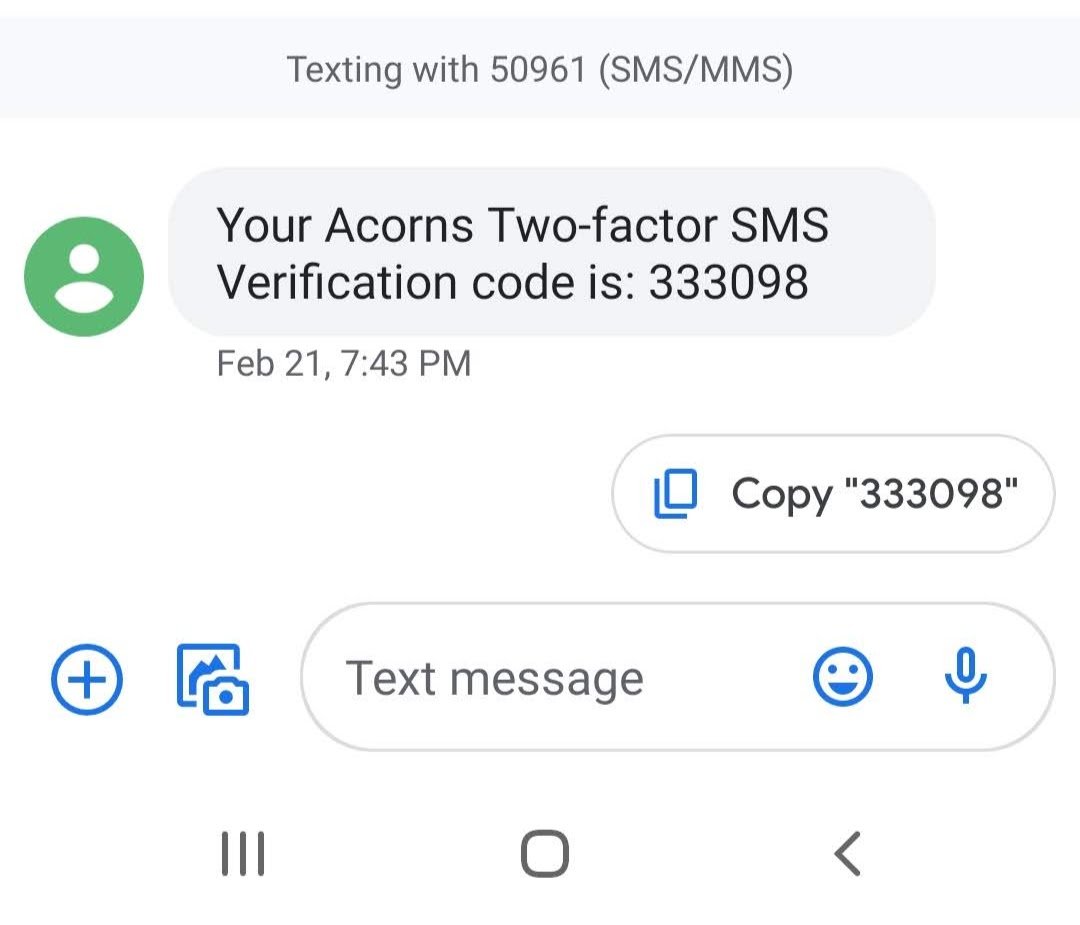
But for those who do choose to secure online accounts with 2FA, there's another issue: many companies only offer using SMS to authenticate you. That means when you try to sign in the first time from a new phone or computer, you receive a text message on the number the company has on file for you. It sounds simple, but it's as bad or worse than not using 2FA at all because of the false sense of security it gives.
It's not really easy to "steal" your phone number by fooling a carrier into giving you a new SIM card because it involves convincing someone to do a thing they aren't supposed to do. But we all know that happens. It's also not easy to intercept an SMS, even though the methods to do so have been around for a long time. But it's simple — and cheap — to pay a company to reroute SMS messages from one number to another.
Businesses do need to forward SMS messages, but there has to be some oversight.
There is a legitimate need for rerouting SMS messages, such as having a help desk offer support through texting using a business landline or virtual number. The problem is that there is no regulation that makes sure the companies that offer such services actually prove you own the number that's being redirected. You simply fill out an online form, send a few dollars, and lie on an application.
This is a huge issue that needs to be addressed, and soon. Many of us will carry the same phone number with us throughout our lives; your phone number really is part of your identity. I don't know how to fix this issue without introducing new laws made by people who have no idea how the technology works or letting this particular industry police itself. Both options here are bad, so I'll let the experts figure it out.
It's not hard to see the enormous threat to safety and security this kind of attack poses. The FCC must use its authority to force phone companies to secure their networks from hackers. Former Chairman Pai's approach of industry self-regulation clearly failed. — Senator Ron Wyden
What I can do though, is say that we all need to stop using services that only offer SMS as a method for 2FA. Period, full stop.
The experts that oversee security at your bank or a retailer or any other service that offers a way to do business online know how bad using SMS for 2FA is. That doesn't seem to make a difference in many cases as you'll find plenty of otherwise reputable businesses that offer it as the only option. I assume it's partially because using SMS for 2FA is easy, and it would cost money to switch the system to use a method that's actually secure.
An authenticator app is just as easy to use as getting SMS codes.
It's equally difficult for many to make that switch, even if they find the right service that offers basic security standards. Using SMS is easy and works from any device that can receive text messages. We all know how it works; get the code in a text, enter the code in the little box, and press submit. It works on a cheap Android phone or even a dumb phone.
What many don't realize is that using something like a software-based 2FA authentication app like Google Authenticator, Authy, or Microsoft Authenticator is just as easy. You don't wait for a code, you open the app and choose the service and one is provided instantly.
Other methods like using a USB or wireless security key are also fairly easy once you find the right hardware that works with your devices, but for most people, using a software authenticator app is the right choice. It's not 100% "hackproof" either, but it's not something that's trivial to exploit.
It's worth switching services to find one that cares about your account security.
Switching how you get your 2FA codes is the easy part, though. What if your bank only uses SMS (or even worse, a voice call) for 2FA? Should you switch banks? Yes. And tell them why you're switching because someone in the IT department knows you're making the right decision to make the switch.
The good news is that most popular services and service providers now offer the option to use an authenticator app. Amazon, Twitter, Google, Apple, Microsoft, and even Facebook will let you use an authenticator app when you set up 2FA or allow you to make changes to the way you get your codes. But there is a real chance that a service you need to use isn't on board just yet and only offers SMS as an option. It's time to ditch those services and find one from a company that cares at least a little bit about your account security.



Post a Comment